Services
How to protect one's property
Services
How to protect one's property

IIoT (Industrial Internet of Things) is a reality today. Its technical basis are intelligent, networked systems, which, in the best case, interact autonomously. This interaction requires trustful cooperation.
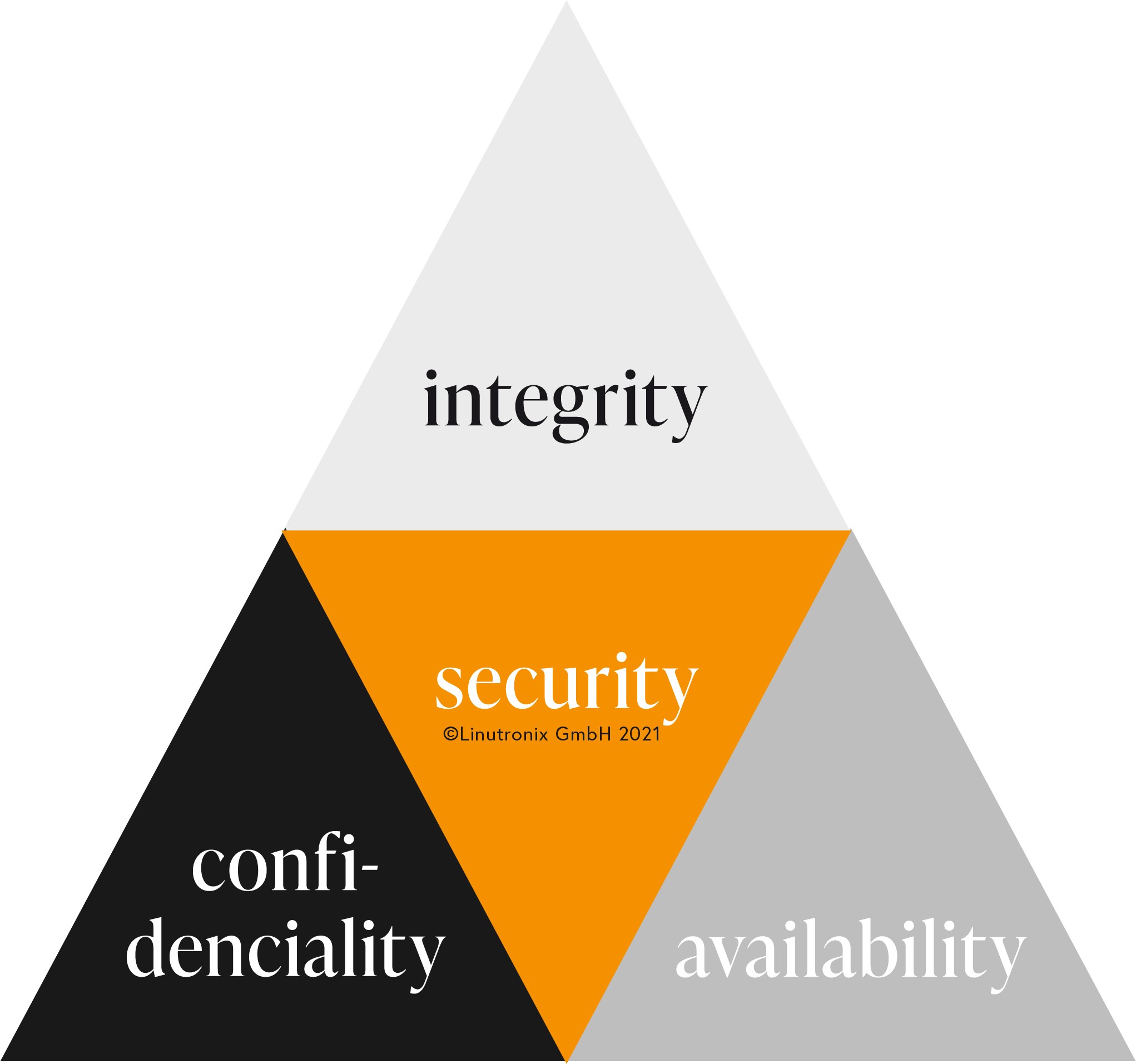
To achieve that, compliance with the following protection goals is required:
| Confidentiality: Data may only be read or modified by authorised users. This applies to both access to stored data and also during data transmission. |
| Integrity: Data must not be changed unnoticed. All changes must be traceable. |
| Availability: Prevention of system failures; access to data must be guaranteed within an agreed time frame. |
In the embedded world, security is often reduced to mere transport security. Current attack scenarios show that there are many more aspects to consider, such as a secure connection and secure access to your embedded system.
In this context, keywords come up, such as secure boot, zero touch onboarding (ZTO), digital certificates, individual encryption and many more. Or Virtual Private Network (VPN) for secure access to the embedded device. Key- and certificate-based access authorization enables a so-called public-key infrastructure (PKI), a powerful tool that also gives you the possibility to effectively protect against loss of access data. In addition, different procedures can be combined to form a multi-factor authentication. The integration of hardware-based procedures such as smartcards and keytokens are also possible.
|
We at Linutronix understand these requirements and are able to work out your personal protection profile together with you and then also implement it in an individually tailored manner. To ensure that your know-how is protected (keyword: copying, unauthorized overproduction) and your data is only designated for you. |