Industrial Grade Linux
Now it's real(ly) time!
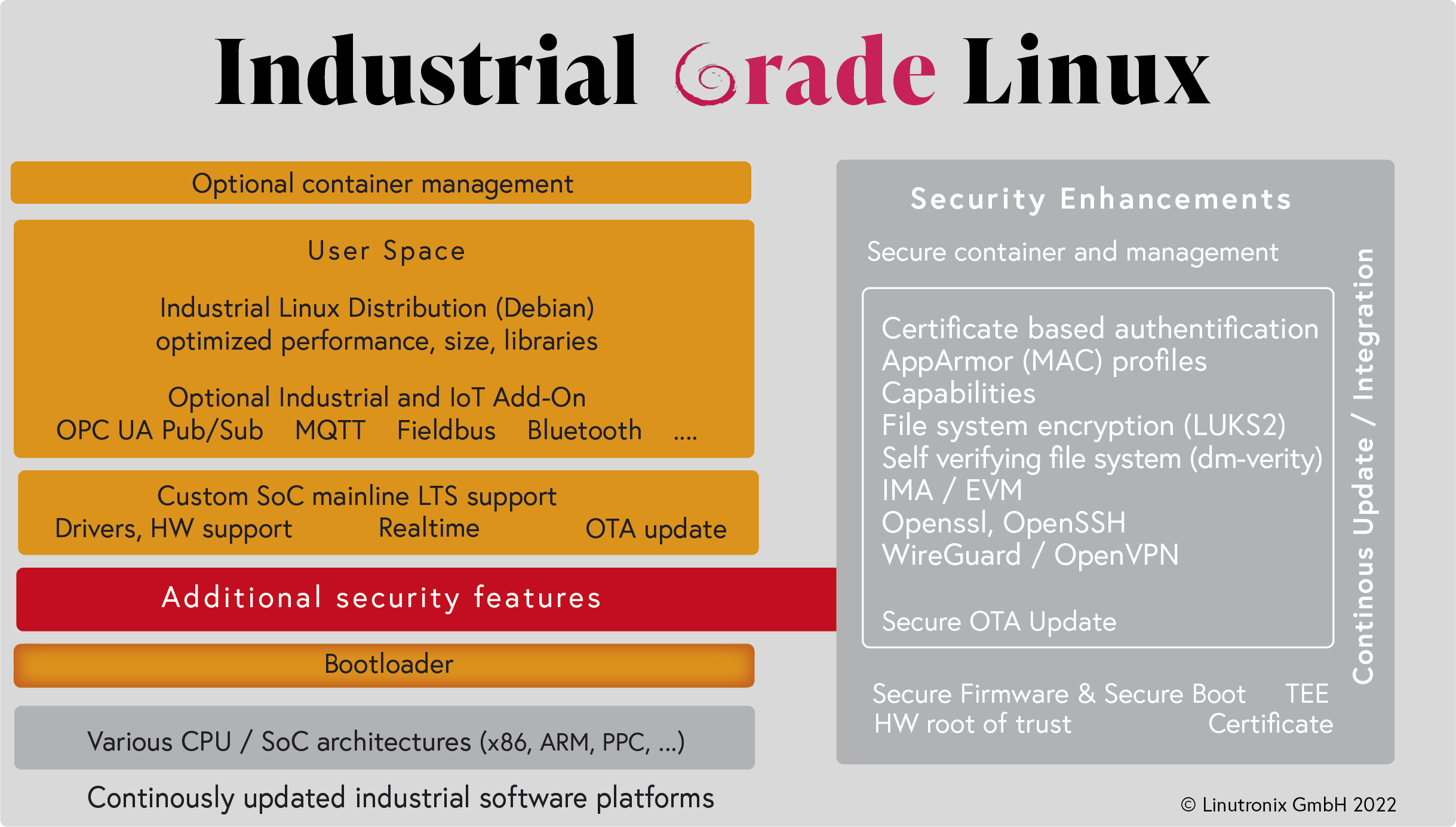
Industrial Grade Linux
Now it's real(ly) time!

Linux offers many possibilities to protect against cyber attacks. This is the result of, among other things, years of operation in data centres. In parallel, more and more functions are now being made available on system-on-chips (SoC) for industry, so that technologies from the server world are now also getting into the factory (virtualisation, containers, etc.).
Determining which of the components should be used, how and in which combination, requires a lot of experience on the Linux side as well as an understanding of the application, of the environment in which this device will be used and also of the business component. Not everything must or can always be achieved. Furthermore, one should never forget that security is not a one-time thing, but must be practised over the entire life cycle of the device.
For more information on this topic, see Life-Cycle Management, Update and IGL Monitoring.
Security should be addressed from the very beginning of the development of a new device. This not only ensures that the right tools are used and the correct measures are implemented, but also that the development processes are set up correctly in order to guarantee security throughout the life cycle. Security also means that the development process must be "safe" in the sense that no malware can be infiltrated during development.
If all components selected are mainline Linux (kernel.org) components, it is ensured that these will remain available in future versions. This provides long-term investment security. And at the same time, all bug fixes and further developments can be taken over from the community.
All components must be adapted to the respective application (hardware, requirements). There aren't any "ready-made" solutions here. However, it helps if the know-how of how to use them is available from many applications.
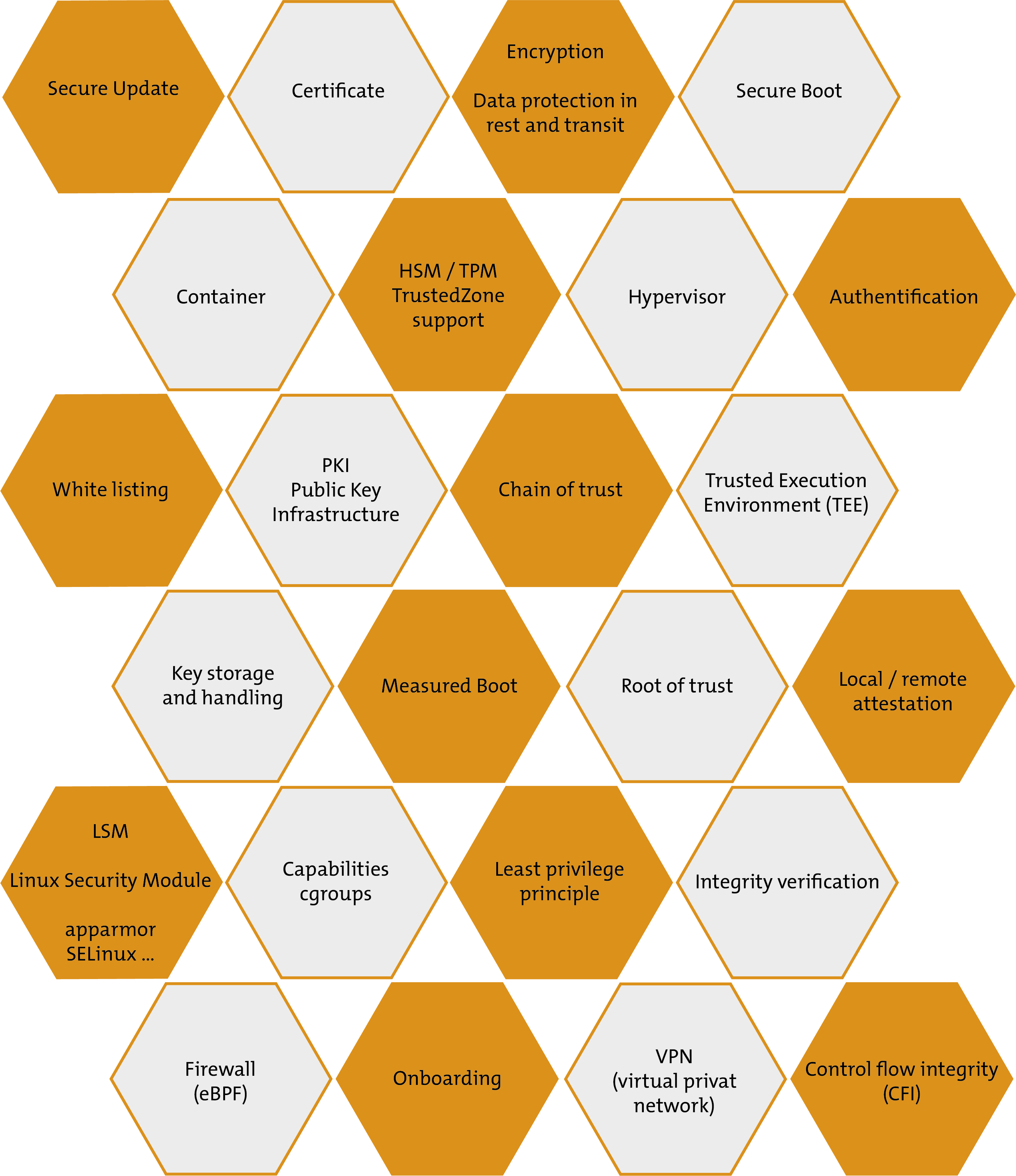
Important components for a secure system include:
A security-optimised solution could be a Secur_OS, as we have defined it in connection with our Industrial Grade Linux. This could look something like this graphic here:
Linutronix offers optional subscriptions for this and for Industrial Grade Linux to provide continuous maintenance, servicing and updating of the BSP.